Cyberattacks are no longer just a threat to large corporations. Small businesses are increasingly becoming targets—often because they’re easier to breach and hold important customer and financial data. That’s why more companies are adopting Zero Trust Security.
Zero Trust is a straightforward yet effective strategy: don’t automatically trust anyone or anything trying to access your systems. Always verify first. Each login, device, and app request undergoes a check before access is allowed. This method helps block unauthorized access and reduces potential damage if something goes wrong.
Zero Trust is a straightforward yet effective strategy: don’t automatically trust anyone or anything trying to access your systems. Always verify first. Each login, device, and app request undergoes a check before access is allowed. This method helps block unauthorized access and reduces potential damage if something goes wrong.
Why Zero Trust Matters For Small Businesses
You don’t have to spend a fortune on IT to be at risk. If you’re storing customer information, processing payments, or working remotely, Zero Trust can significantly enhance your business’s security.
It protects sensitive data.
It keeps customer records, financial information, and internal files safe from phishing, ransomware, and insider threats.
It supports remote and hybrid teams.
Whether your team is working from home, in the office, or on the move, Zero Trust ensures secure access from any device.
It helps with compliance.
If you handle personal or financial data, Zero Trust helps you meet standards like HIPAA, GDPR, and PCI DSS.
It limits damage during a breach.
If a breach does occur, Zero Trust helps contain the threat quickly and prevents it from spreading.
It improves cyber insurance eligibility.
Some insurers now require Zero Trust practices for coverage approval. Without it, you might not be adequately protected.
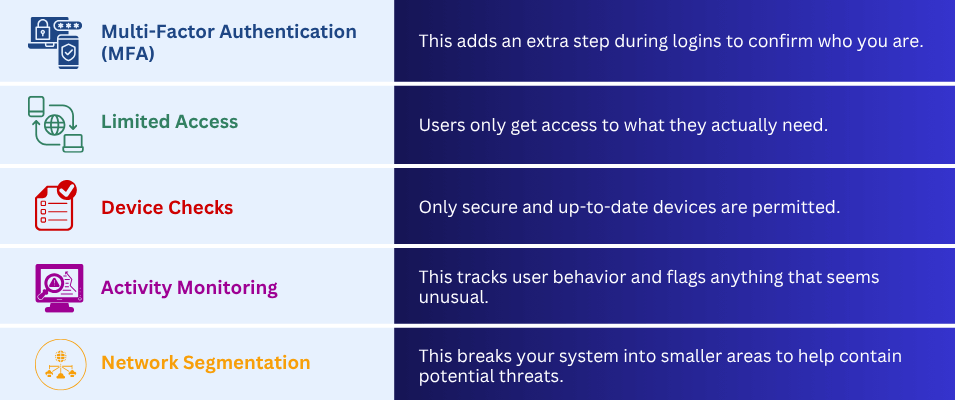
How Zero Trust Works
Zero Trust isn’t just about investing in costly software; it’s about using smart, layered protection. Here are the basics:
Getting Started with Zero Trust
You don’t need an entire IT team to start implementing Zero Trust principles. Just follow these simple steps:
- Turn on MFA for all your accounts.
- Limit access to sensitive files.
- Keep your software and devices updated.
- Use secure cloud storage.
- Train your team to recognize phishing attempts and scams.
Even small changes can lead to significant improvements.
Why It's More Important Than Ever
Cyberattacks are getting more clever. Hackers are using AI to automate phishing, impersonate others, and quickly find weaknesses. That’s why trust can’t just be assumed anymore—it has to be built. Zero Trust is your best bet for staying ahead of these changing threats.
Conclusion
You don’t need to be a tech guru to protect your business. With Zero Trust, you can secure your data, support your team, and meet compliance requirements—without breaking the bank. Always verify. Always protect. That’s what smart security is all about.