Security Operations Center
SOC
What is it and what it does
SOC At a glance
We make sure that our SOC services align with your organization’s security requirements, industry context, and long-term cybersecurity goals. We conduct thorough evaluations, request proposals, and engage in discussions to ensure the value that we bring to your organization’s security posture.
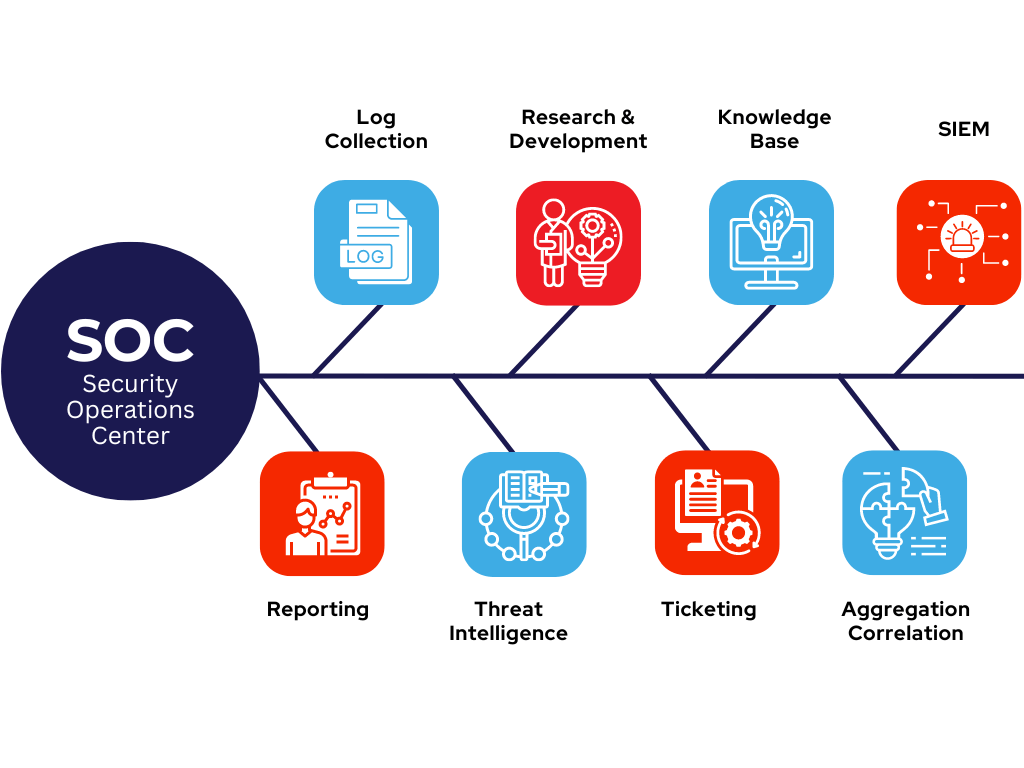
OUR SOC FEATURES
Well-equipped and efficiently operated SOC

- Utilization of monitoring tools to analyze network traffic, system logs, and security events in real-time.
- Integration of Intrusion Detection Systems (IDS), firewalls, and other security appliances for continuous monitoring.
- Implementation of SIEM solutions to collect, correlate, and analyze log data from various sources for anomaly detection and threat identification.
- Correlation of events to provide a holistic view of potential security incidents.
- Automated and manual methods for detecting security incidents promptly.
- Incident response playbooks and workflows for effective and consistent response to security incidents.
- Integration of threat intelligence feeds to stay updated on the latest threats and vulnerabilities.
- Utilization of threat intelligence to enhance detection capabilities and improve incident response.
- Tools and processes to identify, assess, and remediate vulnerabilities in the organization’s systems and applications.
- Patch management systems to ensure timely application of security patches.
- Tools and expertise for forensic analysis of security incidents, aiding in understanding the scope and impact of breaches.
- Use of digital forensics techniques to collect and analyze evidence.
- Integration of automation and orchestration tools to streamline repetitive tasks and response processes.
- Automated incident response actions for known threats.
- Monitoring and analysis of user and entity behavior to detect anomalies and potential insider threats.
- Identification of deviations from normal patterns of behavior.
- Utilization of EDR solutions to monitor and respond to activities on endpoints (computers, servers, etc.).
- Real-time analysis of endpoint activities for the detection of malicious behavior.
- Monitoring and reporting to ensure compliance with industry regulations and internal security policies.
- Documentation of security measures for audit purposes.
- Implementation of programs to educate employees about cybersecurity best practices.
- Regular training sessions to enhance the overall security awareness of the organization.
- Communication and collaboration tools for effective coordination within the SOC team and with other IT and business units.
- Integration with communication platforms for efficient information sharing.
- Generation of regular reports on security metrics, incident statistics, and key performance indicators (KPIs).
- Real-time dashboards for SOC analysts to monitor the current security posture.
- Extension of monitoring capabilities to cover cloud environments, ensuring the security of cloud-based applications and data.
Working with the best team in L.A.
Why TechAssured?
Expertise and Experience
We have a proven track record and experience in cybersecurity and SOC services. We have years of experience working with organizations in various industries, as different sectors may have unique security challenges.
24/7 Monitoring
Our team offers round-the-clock monitoring and incident response capabilities. Cyber threats can occur at any time, and a 24/7 service is essential for timely threat detection and response.
Customization and Tailored Services
We can tailor our services to meet your specific business needs. We believe that a one-size-fits-all approach may not be effective in addressing the unique challenges of your organization.
Threat Intelligence Integration
Our SOC incorporates threat intelligence into our operations. Access to up-to-date threat intelligence can significantly enhance the ability to detect and respond to emerging threats.
Let's Get Started
Ready To Talk?
For immediate support with a cybersecurity incident, please call (310) 861-3633.

Get Your Cybersecurity
Survival Guide
and secure online and offline.

