security information event management
SIEM
What is it and what it does
SIEM At a glance
Here at TechAssured, we deem SIEM as a crucial tool in modern cybersecurity strategies, providing businesses and organizations with the capability to monitor, analyze, and respond to security events in a proactive and efficient manner. SIEM plays vital role in enhancing your company’s overall security posture and is particularly valuable in the context of evolving and sophisticated cyber threats.
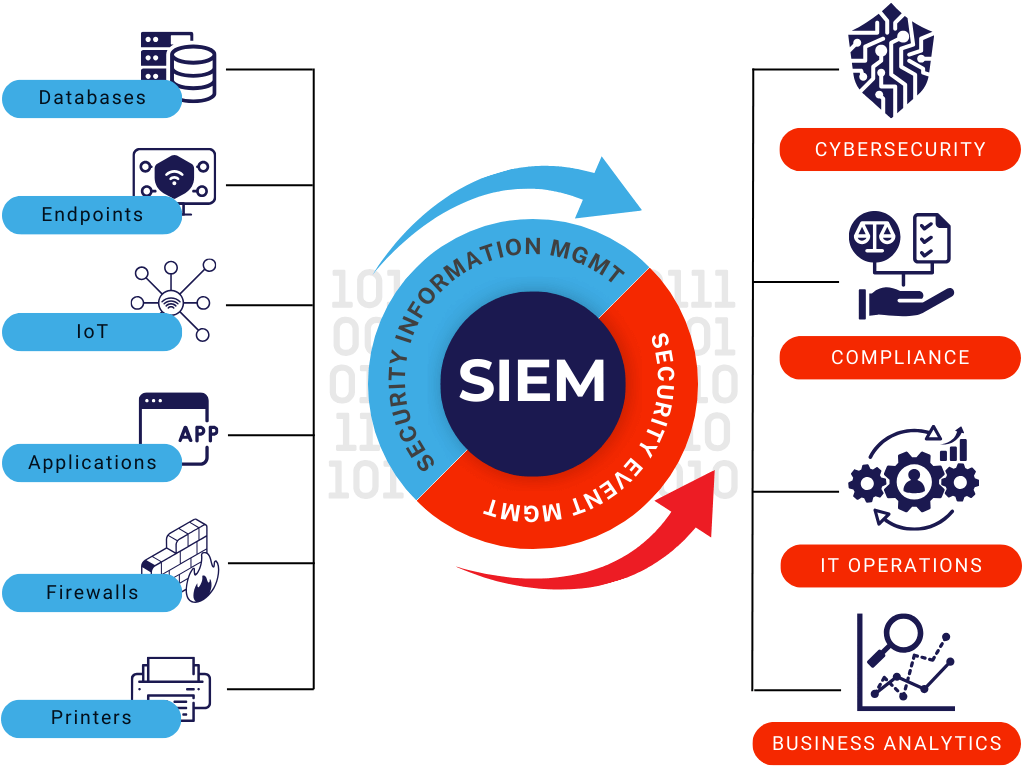
Security Information Management
(SIM)
Security Event Management
(SEM)
technology, process and data
Our SIEM Management Can Positively Impact Your Business
While SIEM offers numerous benefits, it’s important to note that successful implementation and utilization require careful planning, ongoing monitoring, and continuous improvement. We go through methodical procedures to make sure that it well aligns with your organization’s specific needs and keeping the commitment of maintaining a proactive security stance.

Automation: Some SIEM solutions include automation features for routine tasks, reducing the manual workload on security teams and enabling them to focus on more strategic activities.
Incident Response: SIEM facilitates quick and effective incident response by providing real-time alerts and insights into security incidents, enabling organizations to mitigate risks promptly.
Working with the best team in L.A.
Why TechAssured?
Expertise and Knowledge
Our team has specialized knowledge and expertise in the field of security information and event management. We are familiar with various SIEM solutions, their configurations, and best practices for implementation.
Effective Implementation
SIEM implementation requires careful planning and configuration. We can help ensure that the system is set up correctly, integrating seamlessly with your organization's existing infrastructure.
Incident Response and Investigation
We are skilled in incident response and investigation. In the event of a security incident, we can leverage the capabilities of the SIEM system to quickly identify the source, scope, and impact of the incident to minimize the potential damage caused by security breaches.
Cost Optimization
While engaging with TechAssured involves an initial investment, it can lead to cost savings in the long run. We can help optimize the SIEM system's performance, reduce false positives, and enhance the efficiency of incident response, ultimately saving time and resources.
Let's Get Started
Ready To Talk?
For immediate support with a cybersecurity incident, please call (310) 861-3633.

Get Your Cybersecurity
Survival Guide
and secure online and offline.

