Protecting Your Corporate Network
Cybersecurity Services
Cyber Threats - Is Your Business Prepared?
Cyber Threats - Is Your Business Prepared?
Vim soleat eloquentiam in. Porro graecis mei eu, in ius illud dissentiet, vidisse suscipit euripidis est in. Ne paulo feugiat vis, cibo dicat his an. Te sea libris minimum.
secure access service edge
SASE
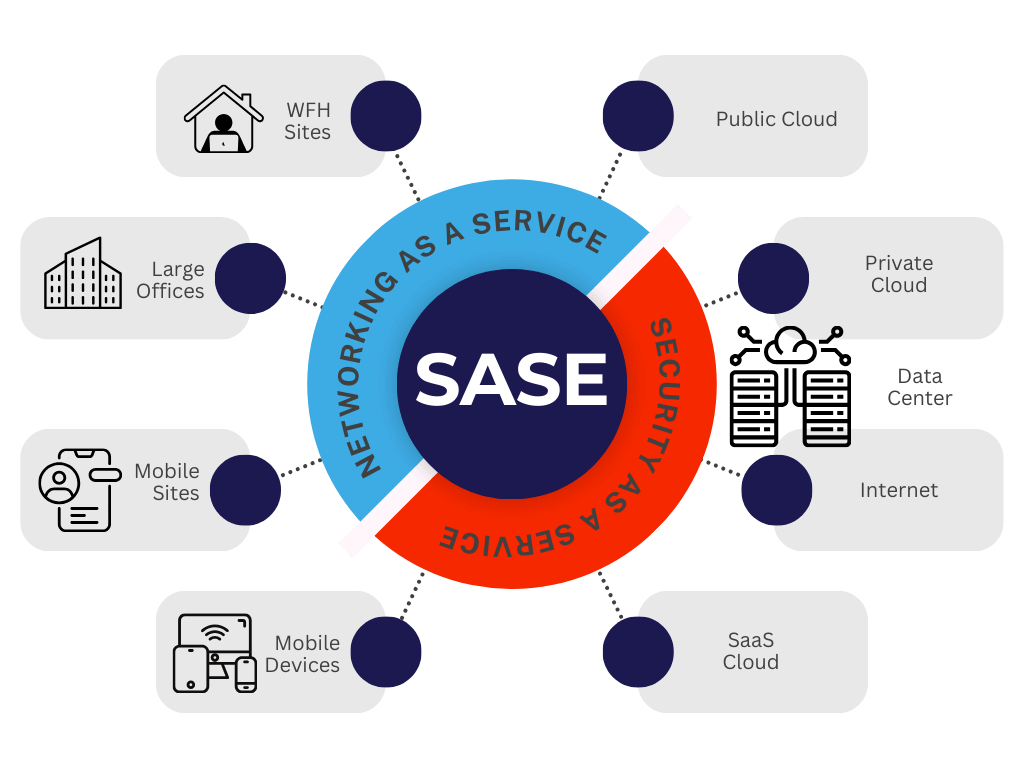
secure access service edge
SASE

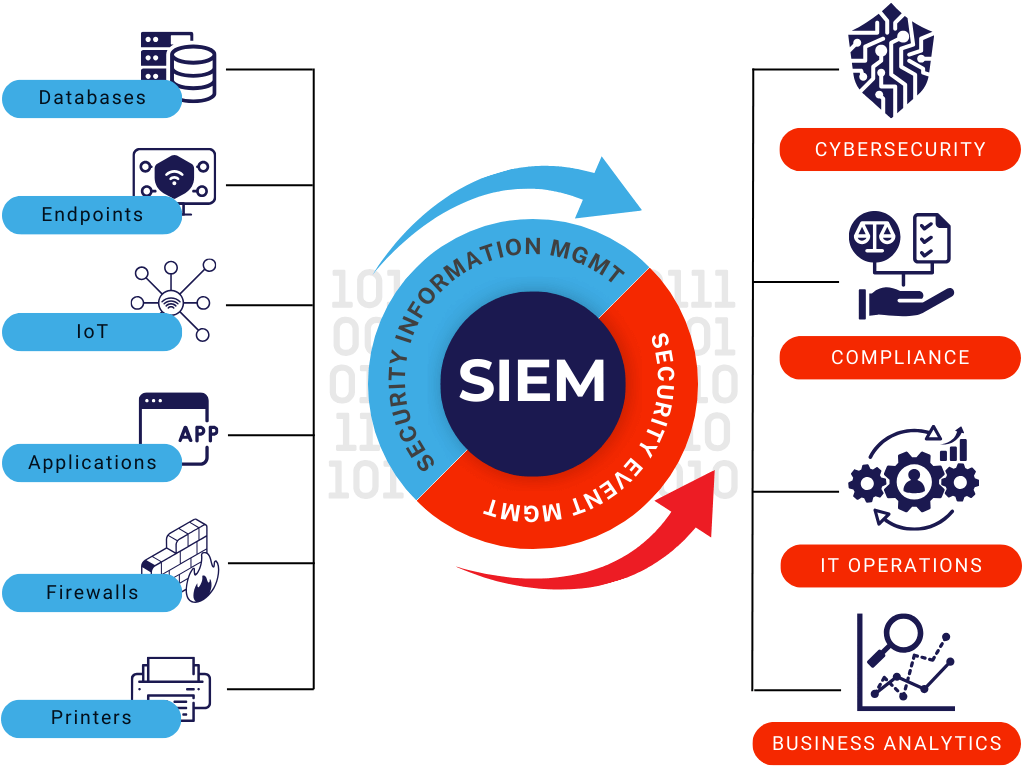
Security Information & Event Management
SIEM
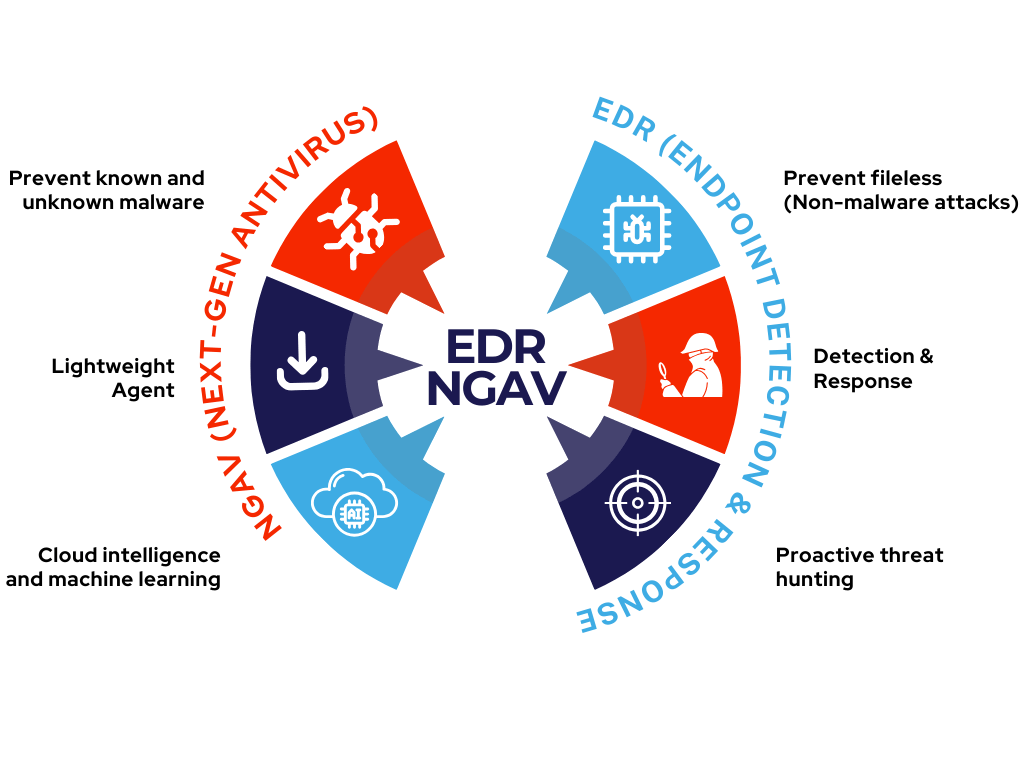
Endpoint Security
EDR / NGAV
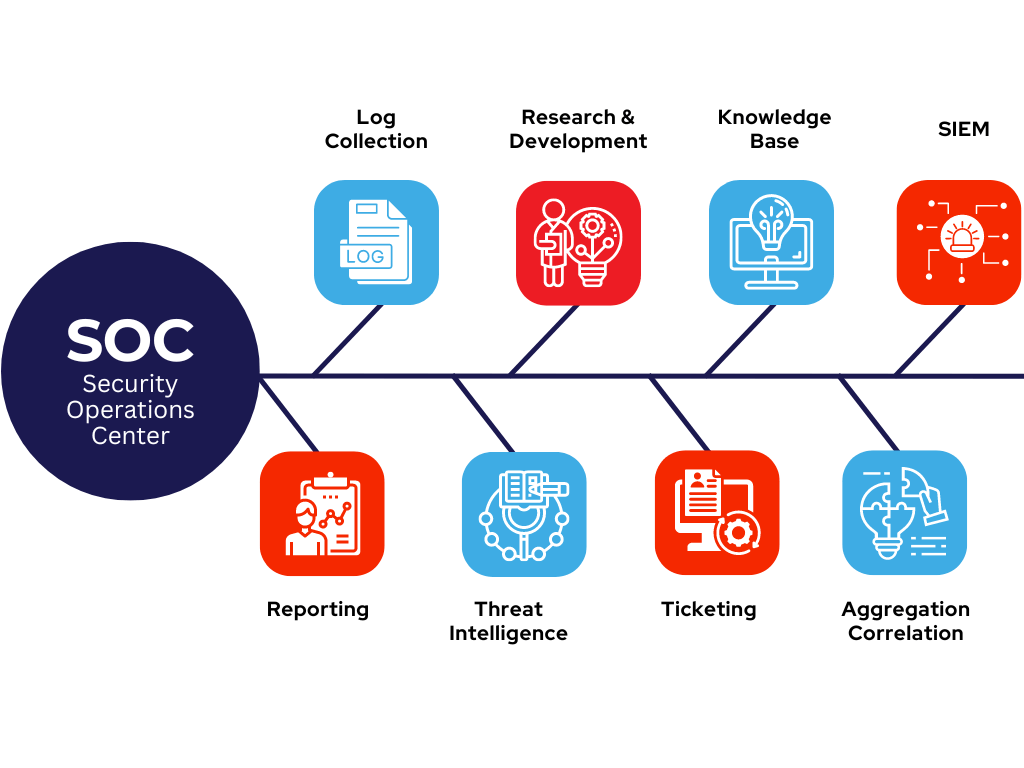
Security Operation Center
SOC
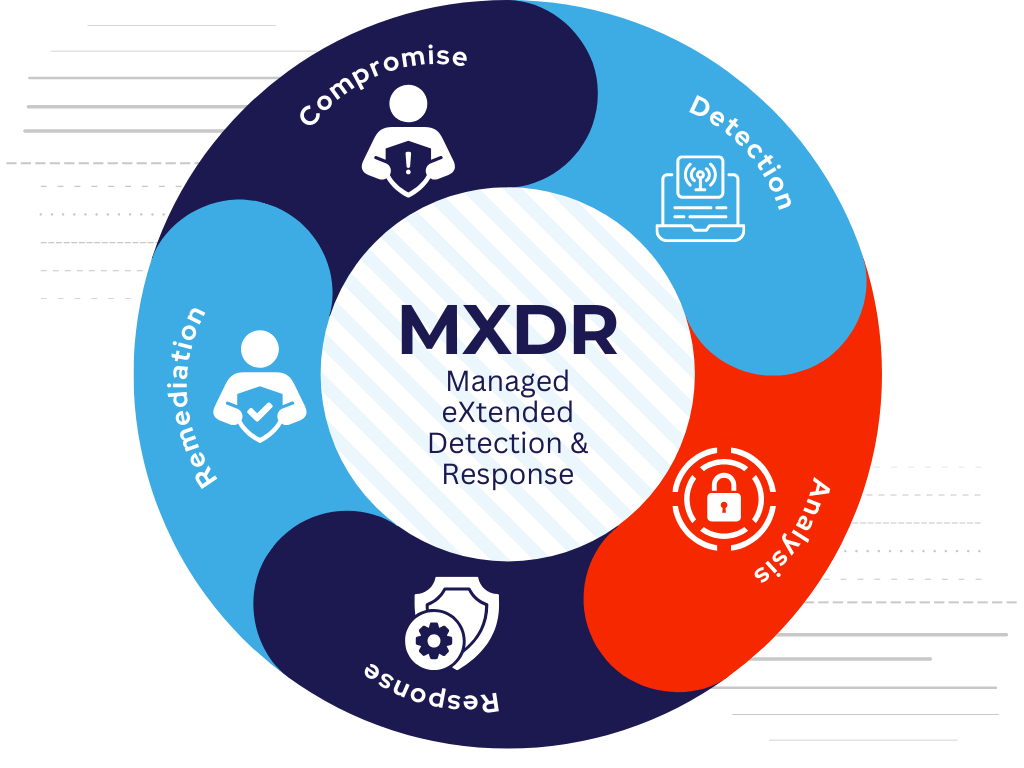
Managed eXtended Detection & Response
MXDR
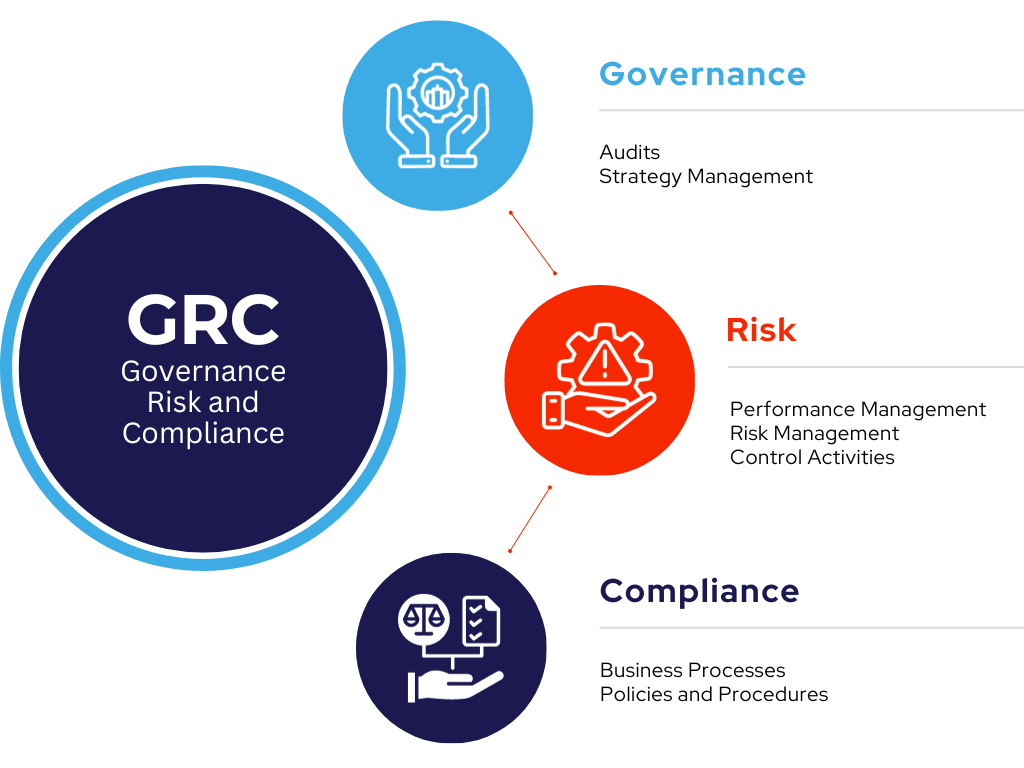
Governance, Risk & Compliance
GRC

Cybersecurity insurance questionnaire assistance and remediation
Security management lifecycle
How We Do It
Managed Services: Getting the most from your solution
Outsource the management and protection of your organization's information technology (IT) security infrastructure to us. Our cybersecurity managed services are designed to enhance your company's security posture, mitigate risks, and respond to cyber threats effectively.
Discovery
Discovery: Cybersecurity strategy and roadmap development
Assessment & Testing
Assessment & Testing: Maintaining a strong cybersecurity defense
Analysis
Analysis: Allocating resources effectively
Implementation
Implementation: Translating cybersecurity strategies
Remediation
Remediation: Resolving cybersecurity incidents
Immediate Cybersecurity Tech Support
Experiencing Security Breaches?
Enhancing your company's resilience
Business Continuity is Our Top Priority

Get Your Cybersecurity
Survival Guide
and secure online and offline.

